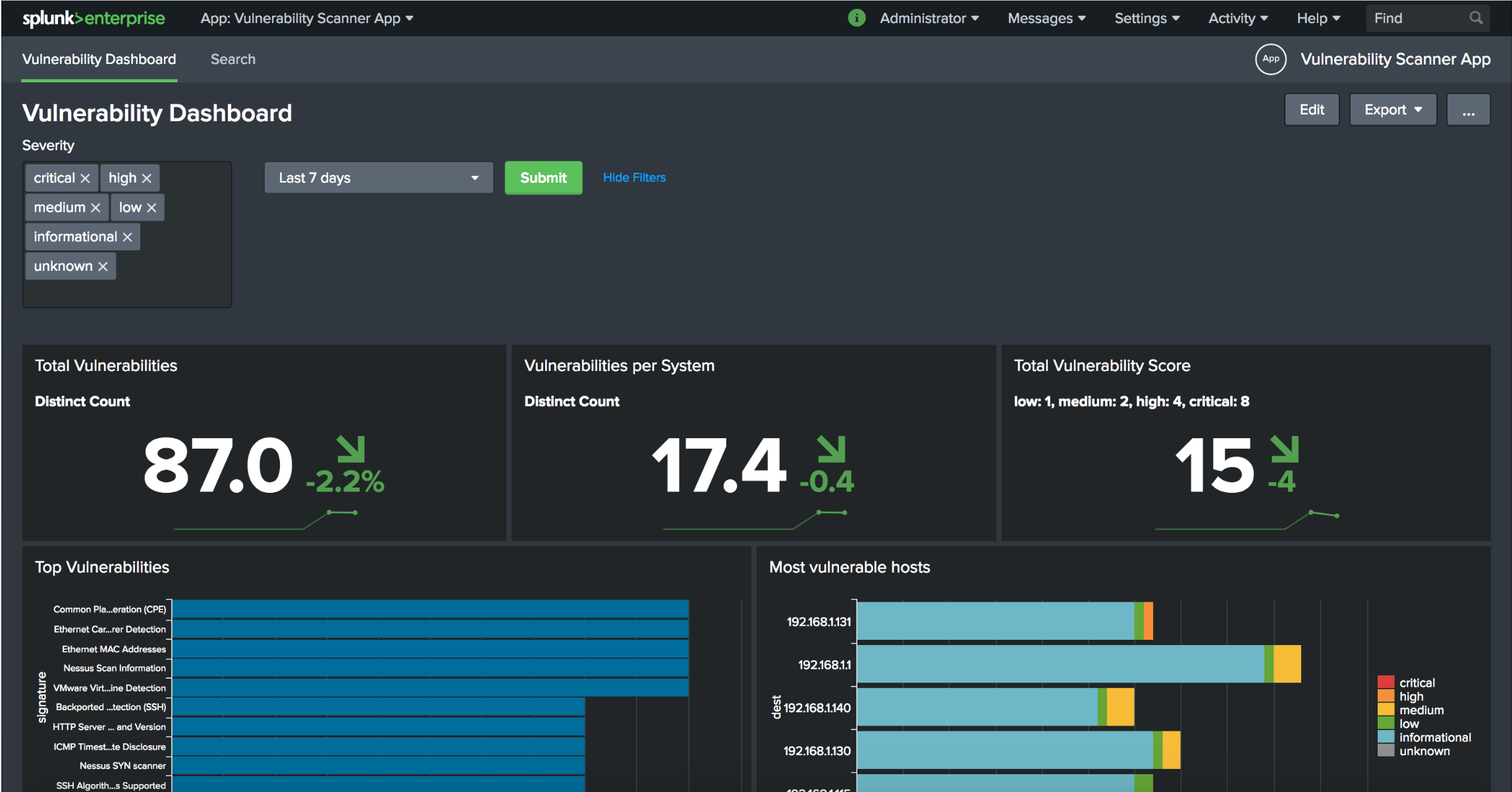
Integrating Nessus Vulnerability Scanner into Splunk
In this blog post, I will explain how to integrate your Nessus vulnerability scan data into Splunk. We will use a single Splunk instance, as described in this blog post. Installation of Nessus can be found here. Configuring your first vulnerability scan is described in this blog post. Splunk is a poweful tool to visualize […]