Sigma vs. TeslaCyrpt
The Sigma repository contains over 200 Sigma detection rules. But we all know, quantity is not equal to quality. That’s why I started a new blog series, in which I will test real malware against a bunch of Sigma detection rules.
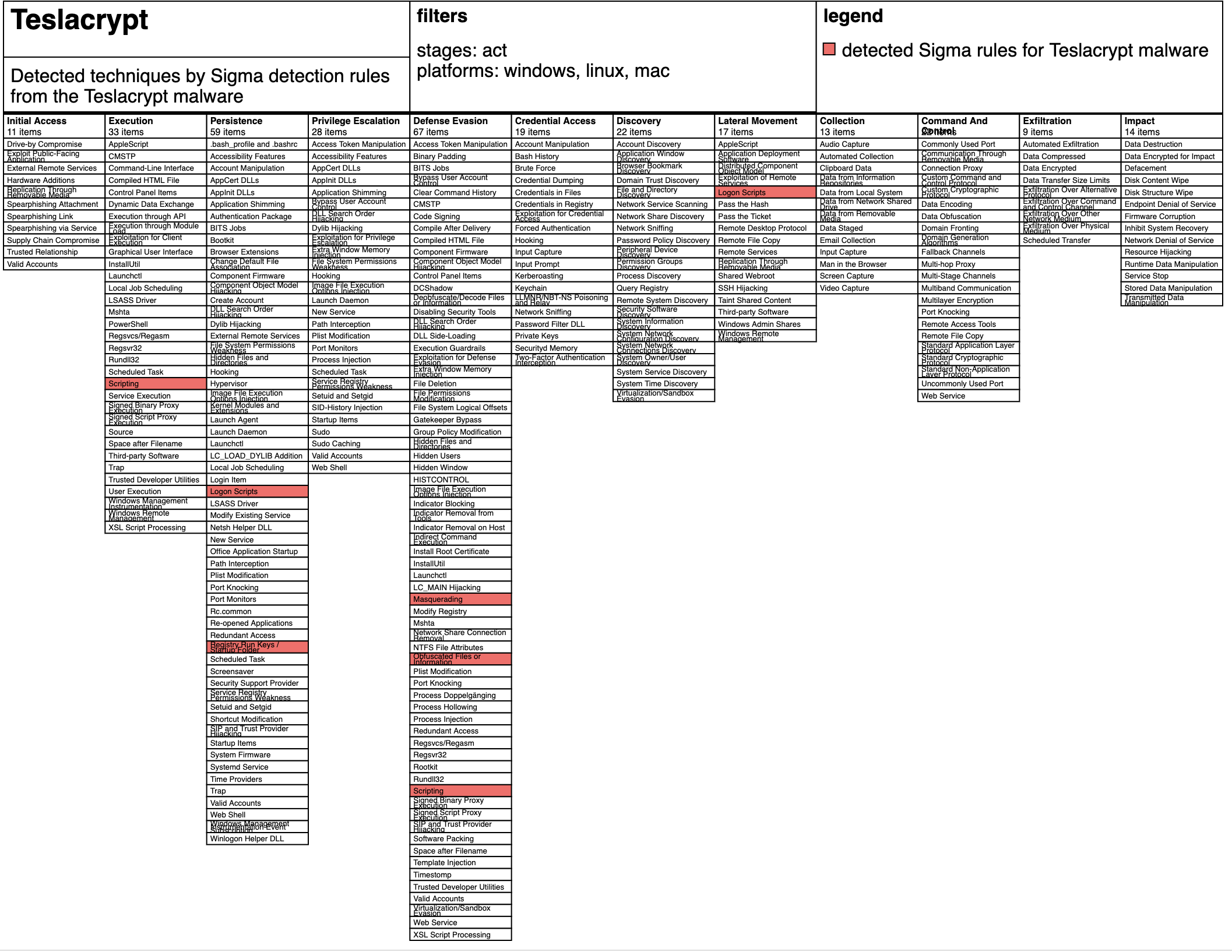
In this blog post, I will test the TeslaCrypt malware against almost all Windows Sigma detection rules from the subfolders builtin, process_creation and sysmon (a total of 192 detection rules). TeslaCrypt is a ransomware that encrypts files saved on the machine and demands payment of a ransom in order to obtain the decryption key.
In order to run the malware in a secure way, I have an isolated malware lab consisting of a victim Windows 7 machine, an Ubuntu machine with INetSim to simulate internet service and a CentOS machine with Splunk:

The Windows 7 Victim is sending its System and Security Event Logs to the Splunk instance. Additionally, Sysmon is configured on the Windows 7 machine to sending its log to the Splunk instance. I’m using SwiftOnSecurity’s Sysmon configuration.
In order to push almost all Windows Sigma detection rules from the subfolders builtin, process_creation and sysmon (a total of 192 detection rules) to the Splunk instance, I used my Sigma2SplunkAlert converter. The triggered alerts are written to the summary index.
I run the Teslacrypt malware for 30mins:

After Teslacrypt was running for a specific time, 6 different Sigma detection rules were able to detect the malware:
- win_proc_wrong_parent
- win_susp_svchost
- sysmon_susp_file_characteristics
- sysmon_ads_executable
- sysmon_susp_run_key_img_folder
- sysmon_logon_scripts_userinitmprlogonscript
The result were stored in the summary index:

I used the mapping from Sigma detection rules to Mitre ATT&CK Techniques in order to calculate a overlay using the ATT&CK Navigator:

Thank you a reading. If I should go more into detail, please let me know.
amazing job appreciate ??
thanks dude!
Thanks so much for the post.Really thank you! Great.