Sigma vs. WannaCry
In this blog post, I will test the WannaCry malware against almost all Windows Sigma detection rules from the subfolders builtin, process_creation and sysmon (a total of 192 detection rules). WannaCry was one of the biggest cyber attacks affecting over 200.000 computers in 150 countries.
In order to run the malware in a secure way, I have an isolated malware lab consisting of a victim Windows 7 machine, an Ubuntu machine with INetSim to simulate internet service and a CentOS machine with Splunk:

The Windows 7 Victim is sending its System and Security Event Logs to the Splunk instance. Additionally, Sysmon is configured on the Windows 7 machine to sending its log to the Splunk instance. I’m using SwiftOnSecurity’s Sysmon configuration.
In order to push almost all Windows Sigma detection rules from the subfolders builtin, process_creation and sysmon (a total of 192 detection rules) to the Splunk instance, I used my Sigma2SplunkAlert converter. The triggered alerts are written to the summary index.
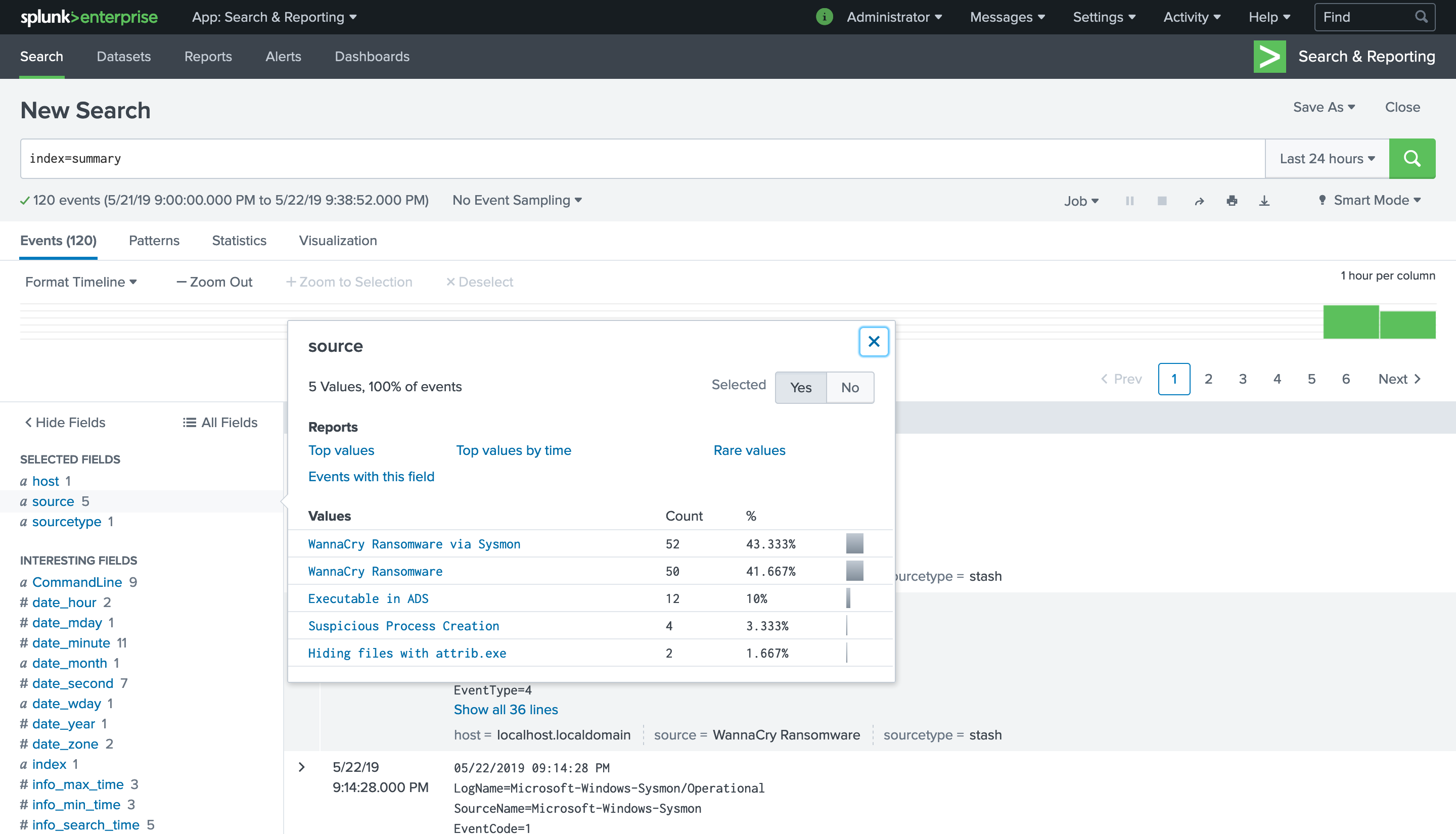
I run the WannaCry malware for 30min. 5 different Sigma rules were detecting the WannaCry malware:
- win_mal_wannacry
- win_malware_wannacry
- sysmon_ads_executable
- win_susp_process_creations
- win_attrib_hiding_files

Thanks for reading.