Sigma2SplunkAlert Tutorial
This blog post is a tutorial about a newly created tool Sigma2SplunkAlert converter. Many Security Operations Center (SOC) are using scheduled searches for their detection rules. Sigma is the new standard for describing detection rules. Deploying multiple Sigma detection rules into Splunk was a time-consuming task. Sigma2SplunkAlert converts multiple Sigma detection rules into a Splunk savedsearches.conf configuration. Additionally, Sigma2SplunkAlert supports Splunk alert actions such as Send email or Add to Triggered Alerts. Sigma2SplunkAlert introduces tokens to use the interesting fields of an alert in the email body. Sigma2SplunkAlert is an open source project on Github:
https://github.com/P4T12ICK/Sigma2SplunkAlert
How it works
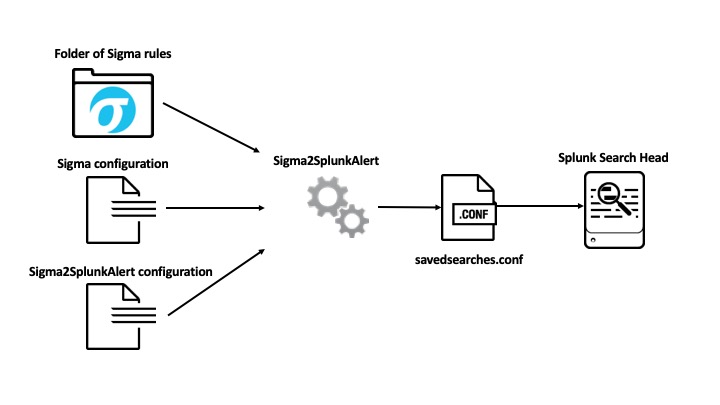
Sigma2SplunkAlert combines Sigma with the power of Jinja2 templating to generate a Splunk savedsearches.conf configuration.

It uses the following inputs:
- folder containing Sigma detection rules
- Sigma configuration file with field names and index mapping (see Sigma repository for more info)
- Sigma2SplunkAlert configuration file containing Splunk alerts configuration values
and generates a savedsearches.conf configuration.
Requirements
Sigma2SplunkAlert needs Sigma for converting the Sigma detection rules into Splunk searches. Sigma needs to be installed and part of the environment variables. Furthermore, Python >= 3.5, PyYAML and Jinja2 is needed. The Sigma2SplunkAlert was tested with Splunk version 7.2.5. If you find some incompatibility to previous Splunk versions, open an issue and I will try to add the support as soon as possible.
Tutorial
In this chapter, we will clone the Github project and convert all the Sysmon rules of the Sigma repository.
We will start with cloning the Sigma2SplunkAlert Github project:
git clone https://github.com/P4T12ICK/Sigma2SplunkAlertSubsequently, we will have a look into the usage by using the following command:
cd Sigma2SplunkAlert
./sigma2splunkalert --help
usage: sigma2splunkalert [-h] [--config CONFIG] [--sigma-config SIGMA_CONFIG]
N [N ...]
Convert Sigma rules to Splunk Alerts savedsearches.conf configuration.
positional arguments:
N folder or file containing the Sigma rules
optional arguments:
-h, --help show this help message and exit
--config CONFIG, -c CONFIG
Sigma2SplunkAlert configuration file
--sigma-config SIGMA_CONFIG, -sc SIGMA_CONFIG
Sigma configuration with field name and index name mappingFirst of all, we will keep the default sigma converter configuration splunk-all.yml under the folder sigma_config. The sigma converter configuration adds SIEM specific information to a Sigma rule. In our case, it adds information about the meta fields index, source and/or sourcetypes. Sigma2SplunkAlert supports only a single sigma converter configuration file, which means that you have to add multiple log sources to a single configuration file in order to convert multiple different log sources in one shot.
Then, we copy the default Sigma2SplunkAlert configuration file and adapt it to our needs:
cp config/config.yml config/config_new.ymlWe will change the scheduling E-Mail address and
Let’s start with changing scheduling to run every 20 minutes over the last 20 minutes:
cron_schedule: '*/20 * * * *'
earliest_time: '-20m'
latest_time: 'now'
app: 'detection_rule_repository'
alert_action:
email:
to: 'test@test.de'
subject: 'Splunk Alert: $name$'
message: 'Use Case $name$ triggered |List of interesting fields: %fields% '
result_link: 0
view_link: 0
include_search: 0
include_trigger: 0
include_trigger_time: 0
inline: 0
sendcsv: 0
sendpdf: 0
sendresults: 0Then, we will change the E-Mail recipient and the E-Mail message:
cron_schedule: '*/20 * * * *'
earliest_time: '-20m'
latest_time: 'now'
app: 'detection_rule_repository'
alert_action:
email:
to: 'ticketing@patrick-bareiss.local'
subject: 'Splunk Alert: $name$'
message: 'Use Case $name$ triggered |List of interesting fields: %fields% '
result_link: 0
view_link: 0
include_search: 0
include_trigger: 0
include_trigger_time: 0
inline: 0
sendcsv: 0
sendpdf: 0
sendresults: 0The characters | in the E-Mail message will be converted to a new line. Additionally, Sigma2SplunkAlert supports token. The token %fields% populates the fields values of the sigma description, e.g. if user is in fields, it will be converted to user: $result.user$. $result.user$ is a Splunk token, which add the value of user to the E-Mail.
Finally, we also want to change some additional E-Mail actions by adding a Link to Alert and Link to Results. A mapping of Splunk alert to the Sigma2SplunkAlert configuration file can be seen in the following image:

Therefore, we will change the options view_link and result_link to 1:
cron_schedule: '*/20 * * * *'
earliest_time: '-20m'
latest_time: 'now'
app: 'detection_rule_repository'
alert_action:
email:
to: 'ticketing@patrick-bareiss.local'
subject: 'Splunk Alert: $name$'
message: 'Use Case $name$ triggered |List of interesting fields: %fields% '
result_link: 1
view_link: 1
include_search: 0
include_trigger: 0
include_trigger_time: 0
inline: 0
sendcsv: 0
sendpdf: 0
sendresults: 0We will use the default sigma converter configuration, our newly created Sigma2SplunkAlert configuration to convert all Sigma sysmon rules (assume that you cloned already the sigma Github repository):
./sigma2splunkalert --config config/config_new.yml ../../forks/sigma/rules/windows/sysmon/Subsequently, we use the output of the Sigma2SplunkAlert converter to store it in the savedsearches.conf configuration in Splunk. After reloading the Splunk configuration, we have all Sysmon Sigma rules as Splunk Alerts:

Thank you for reading.